Zero Trust cybersecurity is a network security model based on a strict identity verification process that only allows authenticated and authorized users and devices access to applications and data. The goal is to eliminate implicit trust and continuously validate every stage of digital interaction to provide the highest level of security possible. In short, zero trust abides by the policy to never trust, always verify.
What are Zero Trust principles and architecture?
In May 2021, President Joe Biden issued executive order 14028, “Improving the Nation’s Cybersecurity,” which triggered the release of three documents to help agencies adopt Zero Trust cybersecurity principles. As a part of these documents, the Office of Management and Budget released a Federal Zero Trust Strategy to adapt civilian agencies’ enterprise security architecture to Zero Trust principles.
The executive order also mandated U.S. Federal Agencies to adhere to NIST 800-207 as a required step for Zero Trust implementation. NIST 800-207 is a published document by the National Institute of Standards and Technology (NIST) which sets up zero trust principles and architecture.
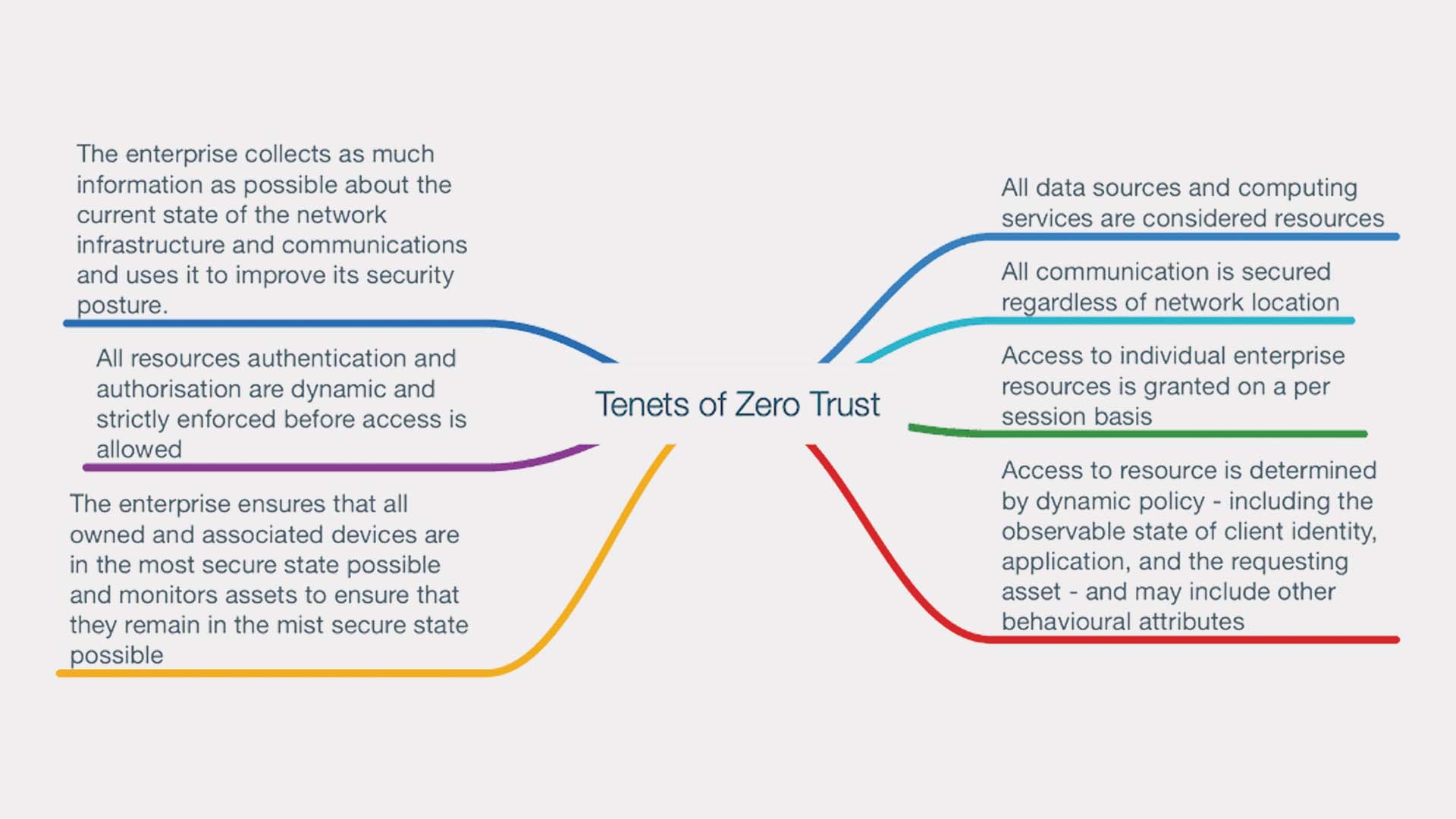
NIST put forth seven basic tenets that every Zero Trust architecture must try to achieve (pictured above). This architecture does not care where your assets are or where your users are, making it intuitively protective. When done correctly, Zero Trust architecture is expected to increase cybersecurity efficacy by 144%.
Why have cybercrimes increased?
The renewed emphasis on Zero Trust security comes from the recent increase of cybercrimes, which have increased 300% since the start of the pandemic. A major driving factor of this is that many entire companies went (and remained) remote, causing many different cybersecurity issues.
For example, many remote employees use insecure, not company-related phones and computers which do not have anti-cybercrime software on them and are thus easier to hack. Additionally, threat actors targeted employees by using COVID-themed phishing and social engineering campaigns to capitalize on the stress and anxiety of the pandemic, often impersonating government and health authorities.
Another pandemic-related increase of cybercrimes is the use of malicious domains to take advantage of the increased demand for medical supplies and information on COVID-19. In this cybercrime, cybercriminals register domain names featuring keywords like “COVID” and pack the websites with malicious activities such as C2 servers, malware deployment, and phishing.

Other than pandemic-related causes, cybercrimes as a whole have increased because of human error, which accounts for about 95 percent of all cyber security breaches. For example, credential stealing and “credential stuffing” in which stolen credentials from one website are used to breach accounts on another site are very common. Also popular are phishing and pretexting in which a victim is tricked into revealing password information and other sensitive data because of a false story created by the hacker.
What can I do to implement Zero Trust and cybersecurity?
There are many easy ways to increase your own cybersecurity and implement Zero Trust principles into your daily life. First of all, avoid reusing passwords; instead, use a password manager to store long and unique passwords for each site. (Believe it or not, the most popular password used in the world is still 123456)
Additionally, enable two-factor authentication on email, social networks, and work sites. Microsoft has actually said that multi-factor authentication would prevent 99.9% of cyberattacks from breaching accounts. You can also enable a Virtual Private Network (VPN) before accessing sites that contain sensitive information to ensure more security.
How can companies implement Zero Trust security?

For larger organizations and businesses, implementing Zero Trust is no easy task. One easy way to do so is by implementing a software platform to automatically perform this heavy lifting. For example, REDPro ZTX, short for Raytheon Enterprise Data Protection & Resiliency Platform Zero Trust Extended, monitors users, devices, networks, workloads, and data in real-time to enforce least-privilege access. This means that it continuously verifies access requests and offers automated commands, control, and response to ensure Zero Trust.